GAO Cybersecurity Review Shows Increased Reliance on Contractors for Key IT Ops
Published: October 07, 2015
Federal agencies are relying increasingly on contractor-operated IT systems for high-value areas that could have “severe or catastrophic” impacts if they were breached or disrupted, according to a recent study by the Government Accountability Office (GAO).
In a recent federal information security report, Agencies Need to Correct Weaknesses and Fully Implement Security Programs, GAO released their latest analysis of information security-related reports and data from 24 federal agencies, their inspectors general, and the Office of Management and Budget (OMB) to assess the current effectiveness of agencies’ information security policies and practices and their implementation of Federal Information Security Management Act (FISMA) requirements.
While the news in GAO’s latest assessment is not all bad, they found persistent weaknesses at 24 federal agencies in implementing information security policies and practices covered under FISMA, illustrating the ongoing challenges agencies face in this high-priority area.
According to the report, most federal agencies continue to have weaknesses in the following areas:
- Limiting, preventing, and detecting inappropriate access to computer resources;
- Managing the configuration of software and hardware;
- Segregating duties to ensure that a single individual does not have control over all key aspects of a computer-related operation;
- Planning for continuity of operations in the event of a disaster or disruption; and
- Implementing agency-wide security management programs that are critical to identifying control deficiencies, resolving problems, and managing risks on an ongoing basis.
GAO also noted that many of the hundreds of recommendations made by GAO and agency inspectors general (IG) to agencies to address deficiencies in their information security controls and weaknesses in their programs remain unimplemented. Each agency’s IG reported weaknesses in the processes used to implement FISMA requirements. GAO found that FISMA evaluation guidance provided to the IGs by the Office of Management and Budget (OMB) and the Department of Homeland Security (DHS) was not always complete, leading to inconsistent application by the IG.
Increased Reliance on Contractor-Operated Systems for High Value Operations
One element of the assessment that caught my attention was a section where GAO provided some data around the number of systems that are agency-operated vs. contractor-operated and where these systems fell according to their importance to agency operations, etc.
For fiscal years (FY) 2013 and 2014, OMB had agencies report the number of agency and contractor systems by “impact levels,” as defined by the National Institute of Standards and Technology (NIST) in their 2004 Federal Information Processing Standards (FIPS) Publication 199, Standards for Security Categorization of Federal Information and Information Systems.
Following FIPS 199, agencies are required to categorize each information system according to the magnitude of harm or impact incurred if the system or its information is compromised. NIST defined three impact levels where the loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect (low), a serious adverse effect (moderate), or a severe or catastrophic adverse effect (high) on organizational operations, organizational assets, or individuals.
For FY 2014, the 24 agencies reported 8,378 agency- and 1,528 contractor-operated systems, for a total 9,906 systems. (See table below.)
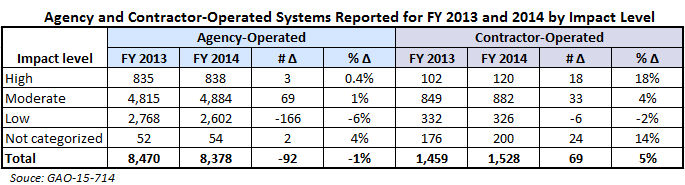
Observations
- Overall agencies reported a 5% increase in reliance on contractor-operated systems, compared to a -1% change for agency-operated systems.
- For high-impact systems, agencies reported operating 3 more systems themselves in FY 2014 compared to FY 2013, but reported 18 more contractor-operated systems. That is nearly a 20% increase year-to-year.
- Agencies reported 6% fewer Low Impact systems overall and these are overwhelmingly dominated by systems they operate themselves.
- Systems tagged as “not categorized” for impact level increased from FY 2013 to FY 2014, with the majority of these systems falling within the contractor-operated realm.
Implications
GAO, OMB, agency IGs, and others will continue to press agencies to improve their information system security posture, and increasingly this includes their supporting contractors. Last year, GAO reported that their review of several federal agencies found that they were inconsistent in overseeing security control assessments of their contractor systems and recommended that the agencies develop procedures for the oversight of contractors.
Agencies that rely on contractor-operated systems for their operations – even if the systems are deemed low-impact by FIPS 199 standards – will continue to ratchet up the requirements on these systems and their supporting contractors. Many federal IT contracting companies, whether large, medium, or small, have been taking steps to harden their security and demonstrate this where possible, but slowly-evolving and sometimes conflicting technical standards and acquisition rules can make it difficult to navigate the landscape and demonstrate compliance.
Firms should anticipate these changes and get ahead of them when possible. Take advantage of opportunities to shape cyber-related aspects of the market and stay aware of how new rules could impact your company and your federal contracts. Failure to do so could jeopardize competiveness for new business and introduce vulnerabilities on existing contracts.