OMB Reports Cybersecurity Incident Data for FY 2016
Published: March 16, 2017
Critical Infrastructure ProtectionCybersecurityOMB
The latest federal information security status report reflects an update to how agencies are measuring cyber-incidents.
The last several years have been challenging for federal agencies in the area of cybersecurity, with revelations of serious breaches and ongoing struggles to improve their security posture. The latest fiscal year (FY) 2016 Federal Information Security Modernization Act of 2014 (FISMA) Annual Report to Congress (FKA the Federal Information Security Management Act report) reflects many of the efforts to improve federal cybersecurity instituted in the final couple of years of the Obama Administration.
In a blog post on the White House Web site announcing the report’s release, Grant Schneider, the Acting Federal Chief Information Security Officer (CISO), highlighted government-wide performance improvements around the key areas of information security continuous monitoring, multi-factor authentication credentialing, and anti-phishing and malware defense capabilities. While the report covers all these areas and more, I will focus here on the cyber-incident aspects discussed in the report.
Updated Cyber-Incident Classifications
Schneider highlighted in his blog that in FY 2016 agencies were required to use “an incident reporting methodology that classifies incidents by the method of attack, known as attack vector, and to specify the impact to the agency,” specified under revised Incident Notification Guidelines set by the Department of Homeland Security's (DHS) U.S. Computer Emergency Readiness Team (US-CERT).
While I usually like to provide some historical comparison of cyber-incident data, the shift US-CERT’s approach makes this difficult. Schneider makes a point to stress that the FY 2016 incident data is not comparable to prior years’ incident data.
The updated US-CERT guidelines break down incidents into the following nine Attack Vectors as described:
- Attrition – Employs brute force methods to compromise, degrade, or destroy systems, networks, or services.
- E-mail/ Phishing – An attack executed via an email message or attachment.
- External/Removable Media – An attack executed from removable media or a peripheral device.
- Impersonation/Spoofing – An attack involving replacement of legitimate content/services with a malicious substitute
- Improper Usage – Any incident resulting from violation of an organization’s acceptable usage policies by an authorized user, excluding the above categories.
- Loss or Theft of Equipment – The loss or theft of a computing device or media used by the organization.
- Web – An attack executed from a website or web-based application.
- Other – An attack method does not fit into any other vector or the cause of attack is unidentified.
- Multiple Attack Vectors – An attack that uses two or more of the above vectors in combination.
According to the report, agencies reported 30,899 cybersecurity incidents to US-CERT in FY 2016, (compared to more than 77K for FY 2015, under the former reporting method.) These incidents break out across the nine Attack Vectors as follows, with the largest number falling into the Other category. (See chart below.)
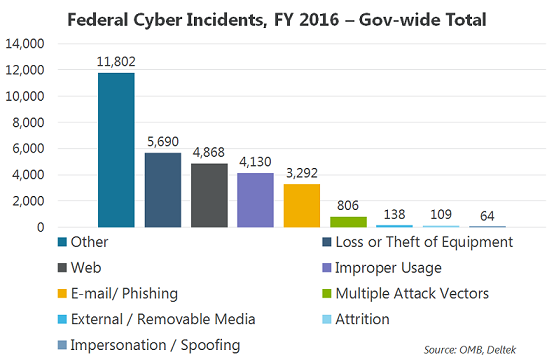
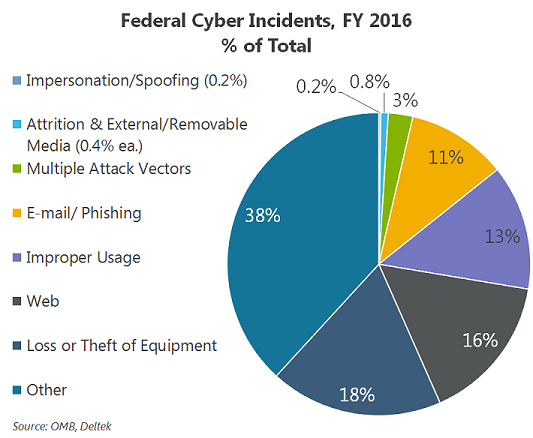
An alternative view of the FY 2016 cyber-incidents is to relate the frequency of each Attach Vector to the whole. (See chart below.)
Implications
Factoring out Other and what could be called “external threats” via the Web internal behavioral elements like Improper Usage and falling prey to E-mail Phishing attacks make up nearly a quarter of last year’s reported incidents. Adding Equipment Loss or Theft brings that total to more than 13,000 incident, more that 40% of the total.
It is noteworthy that 85% of all incidents fell into one of four categories; Other, Loss or Theft of Equipment, Web, or Improper Usage. Even under the new US-CERT reporting methodology, a look back at the incident data from last year seems to suggest some ongoing challenges in both type and frequency continue to linger, especially when looking at the definitions of what is included in each bucket. The Other category as defined above underscores the continued pressure agencies are under to increase their cyber- capabilities.