Federal Cybersecurity Incident Metrics Point to Ongoing Challenges
Published: May 11, 2023
Federal Market AnalysisCybersecurityCISAOMBPolicy and Legislation
The latest federal cybersecurity status report reveals the continued challenge civilian agencies have with incident reporting and policy enforcement.
Cybersecurity remains a top federal technology priority, as the White House, the Office of Management and Budget (OMB), the Cybersecurity and Infrastructure Security Agency (CISA) and other federal agencies continue to take multiple steps to protect federal IT systems and data in the face of persistent threats and challenges. OMB’s latest Fiscal Year 2022 Federal Information Security Modernization Act of 2014 (FISMA) Annual Report to Congress reflects the ongoing challenges that agencies face in both the variety of threats and their internal processes for addressing them.
Reported Federal Cyber Incidents
According to the latest OMB FISMA release, agencies reported 30,659 cybersecurity incidents to the U.S. Computer Emergency Readiness Team (US-CERT) in FY 2022 – down -1,884 (-5.6%) compared to the 32,543 incidents reported in FY 2021 and just 160 incidents (-0.5%) below the 30,819 incidents reported in FY 2020. This puts FY 2022 effectively on-par with FY 2020 levels and reverses the previous two-year trend of agencies having reported increases in incidents. (See chart below.)

Consistent Attack Vector Metrics for FY 2022
OMB’s categories and definitions of Attack Vectors that agencies are to report as part of their FISMA submissions has been consistent since FY 2018, allowing for some year-to-year comparisons. The US-CERT guidelines break down incidents into the following nine Attack Vectors as described below:
- Attrition – Employs brute force methods to compromise, degrade, or destroy systems, networks, or services.
- E-mail/ Phishing – An attack executed via an email message or attachment.
- External/Removable Media – An attack executed from removable media or a peripheral device.
- Impersonation/Spoofing – An attack involving replacement of legitimate content/services with a malicious substitute.
- Improper Usage – Any incident resulting from violation of an organization’s acceptable usage policies by an authorized user, excluding the other categories.
- Loss or Theft of Equipment – The loss or theft of a computing device or media used by the organization.
- Web – An attack executed from a website or web-based application.
- Other / Unknown – An attack method does not fit into any other vector or the cause of attack is unidentified.
- Multiple Attack Vectors – An attack that uses two or more of the above vectors in combination.
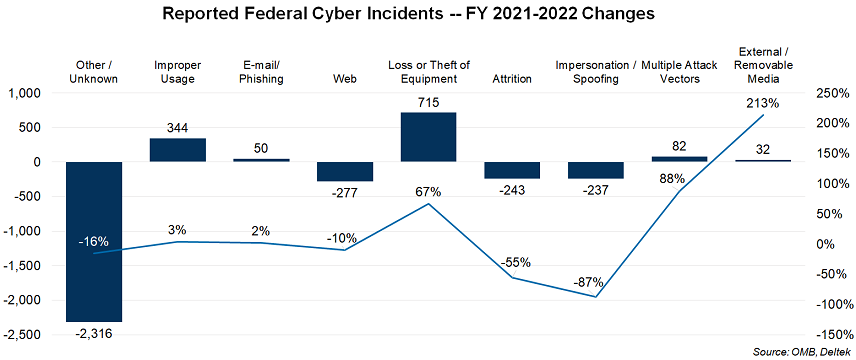
For FY 2022, these incidents break out across the nine Attack Vectors as follows, with the largest number falling into the Other/Unknown category and the smallest number in Impersonation/Spoofing. (See chart below.)

An alternative view of the FY 2022 cyber-incidents is to relate the relative frequency of each Attach Vector to the whole. (See chart below.)

Year-to-year changes from FY 2021 to FY 2022 in the frequency of the top Attack Vectors reveals the areas where agencies continue to experience some of the greatest challenges and where they have gained some ground.
In FY 2022, the Other/Unknown vector accounted for the highest number (12,489) and proportion (41%) of reported incidents, indicating that federal agencies continue to be challenged to appropriately categorize incident vectors during reporting or fail to update their initial reporting once more clarity is gained during their investigation. To further improve the quality of incident reporting data in FY 2023 and beyond, “CISA will provide OMB with data regarding both individual agencies’ performance in providing accurate, machine-readable data to CISA, as well as any gaps CISA has in receiving, updating, or maintaining such records,” according to the report.
However, the current Other/Unknown data shows some signs of improvement. Compared to the 14,805 incidents reported for FY 2021, the FY 2022 level represents a 16% year-to-year decrease, indicating agencies gained some effectiveness in categorizing cyber incidents. Most of the other areas of year-to-year improvement, i.e., decreasing proportions, are among the less-reported incident areas, such as Web, Attrition and Impersonation/Spoofing.
As for other ongoing challenges, the FY 2022 data indicates that agencies continue to struggle with Improper Usage (IU) violations by authorized users. This vector has consistently remained near or at the top of the frequency list each year since FY 2018 and accounts for 34% of incidents for FY 2022, up from 31% in FY 2021. IU had previously decreased by 15% from FY 2020 to FY 2021, but the FY 2022 level reverses some of that with a 3% increase in incidents from FY 2021. Given that IU incidents result from an authorized user’s violation of their organization’s acceptable usage policies (excluding actions captured by other incident categories) the year-to-year fluctuation, and FY 2022 increase, indicate that agencies have sustained opportunities to increase their user cyber training and education and policy enforcement efforts. According to OMB, the IU data “suggest that although agencies have processes or capabilities that detect when a security policy is being violated, many lack automated enforcement or prevention mechanisms.”
After four straight years of declining reported incidents, E-mail/Phishing saw a 2% increase from FY 2021 and accounted for 10% of cyber incidents in FY 2022, up from 9% in FY 2021. Loss or Theft of Equipment saw an even higher increase from FY 2021 to 2022, growing from 3% of total incidents to 8% – a 67% year-to-year increase.
Similarly, incidents related to External/Removable Media and Multiple Attack Vectors both increased significantly from FY 2021, underscoring the persistence of these threat vectors, but these remain a small portion of total incidents overall. (See chart below.)
Overall, the findings, and CISA’s and OMB’s plans to address areas of ongoing incident challenges, (e.g., the Other/Unknown category), are not substantively different from what OMB said in last year’s report, and the year before that. While this might call into question the relevance or effectiveness of these measures, it underscores the incremental and evolutionary nature of improving agency cybersecurity practices and the need for sustained diligence.